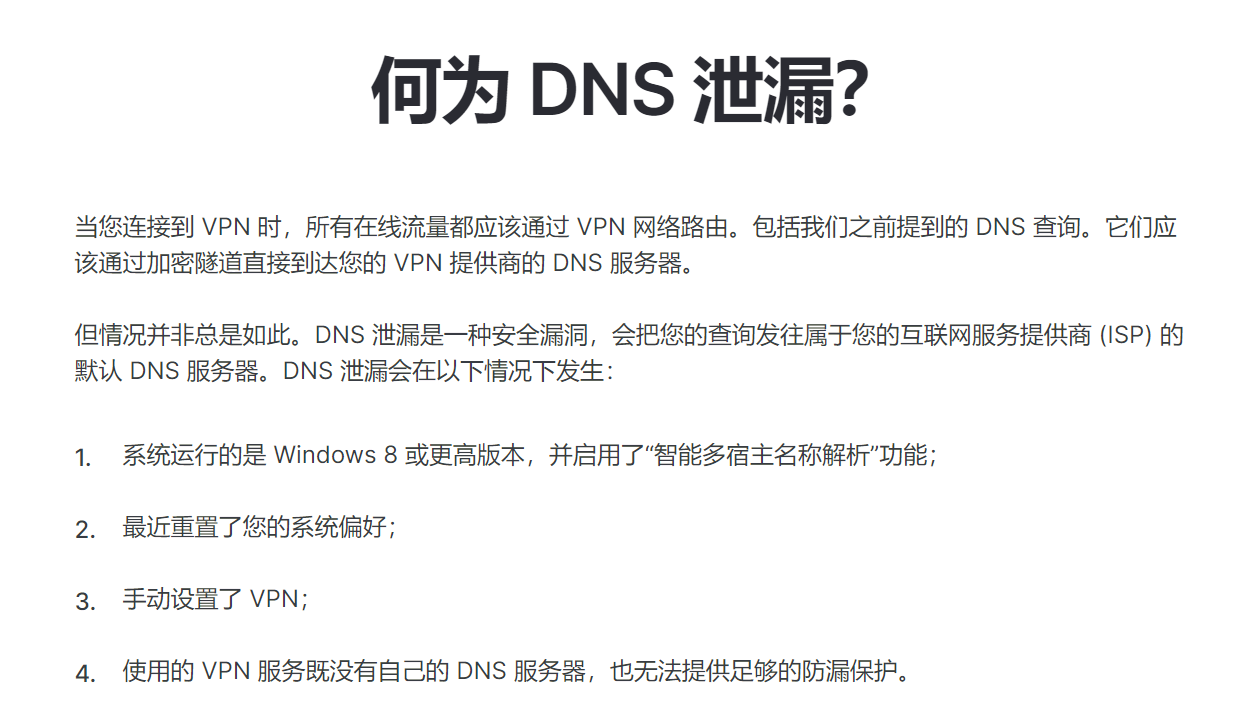
关于DNS泄漏

DNS泄漏基础概念

方案:Adguard Home自建DNS搭配Adguard客户端
如果能搭配Adguard Home,使用自己的DoH服务,安全性就大大增加。而且就我的体验,Adguard Home 服务端上游DNS使用DNS Pod效果也是非常好,也不会返回污染的地址。可参考我的文章:

然后PC端或者手机端使用Adguard客户端,且配置非默认端口的加密DNS,防止端口被封。这将极大提升DNS查询私密性,虽然不能做到100%,但对于普通人已经是够用了,我们又不去干违法乱纪的事情。
Windows
1.Adaguard 官方也针对Windows版Adguard 使用上可能存在的DNS泄漏写了一篇文章,详细说明了DNS泄漏存在的原因,以及可能的补充配置。

事实上,我认为使用DNS Pod这类公司的公共解析,退一万步,也是比运营商的更好,个人意见而已。如果你能找到更好的可用的DNS服务当然更好,只是,就我这几年的摸索,国外的DNS服务商,要不就是被封、要不就是对国内的应用反馈的都是亚太地区的IP,导致速度非常慢,都影响了正常使用了,还有什么意义?
2.智能多宿主名称解析
NordVPN网站提到,“系统运行的是 Windows 8 或更高版本,并启用了“智能多宿主名称解析”功能,该功能“将DNS请求发送到所有可用的DNS服务器,并且 接受来自 哪个DNS服务器最先响应.”将会有可能导致DNS泄漏,那么这个能够有必要关闭吗?
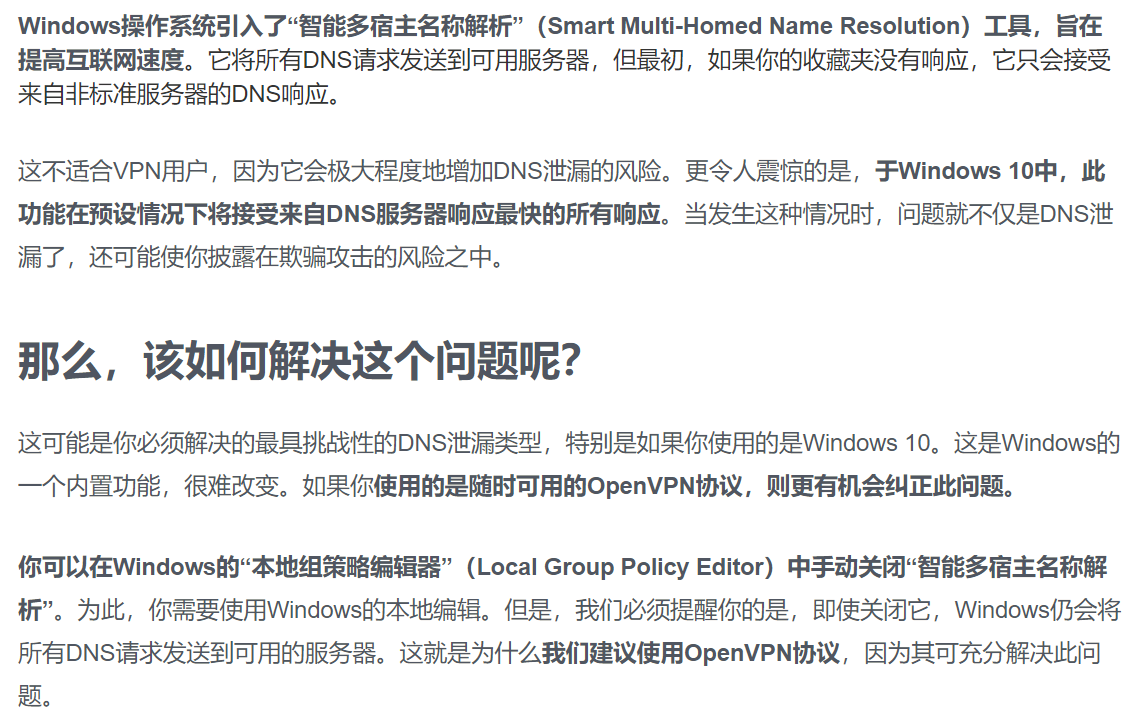
基本上无解。
关于DoH
Yes, the DoH resolver receives encrypted queries from the user. But when it sends those queries on to regular DNS authoritative name servers the query is not encrypted. Thus, DoH does not perform end-to-end encryption. And DoH does not really prevent an ISP from tracking your DNS requests. That’s because after your web browser receives the IP address from the DNS and sends you there, an ISP can see that IP address of your destination site if that site uses HTTP. And there are non-encrypted parts of HTTPS requests that are still in cleartext, like the IP address and Server Name Indication. Thus, using DoH will not prevent a determined ISP (or oppressive government) from knowing where you are going on the web.
按照上面文章的说法,DoH的IP查询并不是完全的隐秘,而DoT的安全性则更高。
There are other options for privacy when using DNS. These include using Domain Name System Security Extensions (DNSSEC) or DNS-over-TLS (DoT). These solutions encrypt DNS instead of partially hiding DNS traffic inside HTTPS.
关于DoQ

Adaugrad 的博客对DoQ作了详细的总结。节选了总结内容如下:
In short, here are the main advantages of DNS-over-QUIC:
1.It encrypts DNS traffic. Nobody except you can see what websites you visit.
2.QUIC is designed to solve the problem of "head-of-line-blocking", that is, it will work better in networks with a high packet loss rate (think mobile data in elevators or tunnels).
3.The QUIC standard supports the so-called "Connection Migration". When you're leaving home and your phone switches from Wi-Fi to mobile network, the QUIC connection, unlike other connections, doesn't drop. Unfortunately, it hasn't been implemented yet, but we hope the situation changes soon.
4.QUIC allows you to establish a network connection much faster. As with the "Connection Migration", it's especially useful when being on mobile. With DNS-over-QUIC implemented, the connection is established twice as fast as with DNS-over-TLS.
然后我搜到这篇文章,这是一份严谨的论文,总结就是,DoH/DoT都不能彻底解决Dns泄漏问题,而经过测试,DoQ也不能彻底解决。哎,这个世道。
https://dl.acm.org/doi/abs/10.1145/3488658.3493782
Increased demand for DNS privacy has driven the creation of several encrypted DNS protocols, such as DNS over HTTPS (DoH), DNS over TLS (DoT), and DNS over QUIC (DoQ). Recently, the DoT and DoH have been deployed by some vendors like Google and Cloudflare. However, it is pointed out that DoT/DoH still have privacy leakage problems. Our goal is aiming at comparing the level of privacy leakage in encrypted DNS. This preliminary work focuses on analyzing the DoQ traffic to determine whether the adversary can infer the category of websites users visit. We find that information leakage is still possible even in the DoQ traffic. Moreover, we identify that important features are mainly related to inter-arrival times of queries, and the accuracy score slightly decreases for more categories.








Comments ()